Offensive Security Certified Professional & PWK – My Experience
Hello guys. Its been a long time coming since I last posted on here and I apologize for the delay. Personal life and my job takes priority over work though, so I hope you can forgive me for this and I’ll get back to posting tutorials related to exploitation and reverse engineering soon.
There are a ton of certification’s in the information security space. While some certifications are ‘good’ and some are ‘bad’, often it’s more a case of different certs for different purposes. If you want to tick a box on a resume you go for CEH, if you want to focus on the theoretical side you go for CISSP, if your boss is paying you go for SANS, and if you want to learn you go for Offensive Security.
In 2013 I received the CEH certification and after reading all the horror stories about the exam on the internet I was not impressed. For someone with a diverse technical background the CEH was “Mickey Mouse” and pretty much a cake walk. Don’t get me wrong I am quite proud to call myself a CEH but I wanted a challenge … something that didn’t just take time and effort, but something that would drag my mind through hell. I found this challenge in the form of the Offensive Security PWK course and OSCP challenge, in my opinion Offensive Security offers by far the best value for money certifications on the market today.
About a few weeks ago I passed my OSCP exam. I would like to share my experience considering this is one of the most interesting, challenging and hardest courses I’ve ever took. The course itself is very comprehensive, but you will need to put in a a lot more effort than just going through the course manual to pass the exam. Be prepared to Try Harder!.
Short Description about Offensive Security Certified Professional.
The “Offensive Security” is unlike any other ethical hacking course that exist today. From the comfort of your own home, you’ll be able to learn and gain knowledge of important skills and techniques that is required for today’s security professional in protecting their networks by applying offensive security. From scanning to enumerating, to password cracking to creating your own exploit, this basic course covers it all.
You will have the options to connect Offensive Security lab remotely and apply your newly developed skills. How awesome is that. You really get a feel of the real thing. I must say, before taking this course I was skeptical –will I understand the materials, if I get stuck on a topic, will I be able to get some help, will I have the time to attend the course from my busy schedule. Well this Offensive Security folks really put their time and effort in tailoring this course for people exactly like me.
No multiple choice, no vague questions, only pure hands-on hacking to an unfamiliar network. Upon completion, you will earn the Offensive Security Certified Professional (OSCP) which demonstrates your competency in the penetration testing field. Which makes this certification distinctive from any other such as the CEH in where it actually proves practical ethical hacking skills.
Once the course starts, the student gets an e-mail with access to the course material (video and PDF) and access to an online lab, you are given access to a lab environment with around 60 machines of varying operating systems, patch levels, and vulnerabilities.
Through out the course, the student gets to follow the teacher and practice on live hosts (in secure and legal environment). Students get the chance to run scans, exploits and other techniques on various operating systems. Course covers a lot of techniques and exercises, but know that most of your time will be spent within the practice lab network. This is a real challenge where you will have to compromise multiple networks using pivoting techniques to succeed.
I cannot stress how much I’ve learned from this course. This might be because I’ve tried to use as little Metasploit as possible and instead done everything I could manually. Enumeration, hunting vulnerabilities and compiling exploits. It felt more reasonable to go with this approach to gain a deeper understanding on how stuff really were executed and finally exploited. While Metasploit makes life easier and various vulnerability scanners save a lot of time when doing penetration tests they are both equally useless when they do not work or report false postives and/or true negatives. If you can’t sort through that information you will not be very successful in the field.
Depending on how much you’ve studied the material owning the “low hanging fruit” will not be very hard. However, when they are owned and forgotten things will start to become a lot harder. In fact, sometimes it will feel like someone hit you on the toe with a sledgehammer. This is when you got to remember that pain is only the weakness leaving the body and you need to try again and this time, try harder.
Once all the exercises completed, an exam is scheduled. There is no multiple choice or question based exam, this final exam requires you to gain access to a certain number of machines within a 24 hour time period. There are a lot of questions that surround the PWK course and OSCP exam/certification. Upon completion of the exam, the fail or pass e-mail is sent within 72 hours.
Pre-requisites:
- A solid understanding of TCP and UDP networking protocols, and know how to read through a packet capture.
- Be familiar with different services: DNS, SNMP, SMTP, SMB, HTTP, and FTP (among others). Be able to read through packet captures most of those services.
- Be comfortable with scripting and get your hands dirty with Python and Shell scripting it will help you a lot..
- Be comfortable with Linux and Windows command line syntax and tools.
- Be familiar with Assembly and a debugger.
- Be prepared to work around 20 hours a week on this, this can be challenging to do next to a fulltime job.
- Web Application Programming experience should be really helpful, as you can grasp it quickly.
- Self Learning is very important.
- Database knowledge is Advantage, You may get situations where it will be necessary.
- Be prepared to Try Harder, this course isn’t a SANS or CEH course where you just fill in a multiple choice exam.
- There is a reason few people pass the exam from the first time.It’s very important that you take good notes and supporting screenshots while hitting the lab. I like KeepNote, which was recommended by Offensive Security during the course. I also installed shutter on my machine to take screenshots. It’s similar to the snipping tool in Windows.
- Take a good backup. I accidently removed part of my notes. The easiest way in my opinion is to use a git repo and regularly push and commit your notes/binaries/scripts or whatever you made to your repo (I used Ubuntu cloud one to sync). It’s easier to track what you have been doing and lowers the risk of deleting things by accident.
My recommendations:
- Script as much as possible in re-usable way.
- Automate all the things, It may save your golden time during exam.
- Make sure you understand every exploit you use, if it’s a Metasploit module, ensure that you can port it to a standalone version.
- Make sure you have a windows environment to compile binaries, cross compiling sometimes gave me a lot of headaches which were quickly solved by using Windows with Visual Studio and codeblocks.
- Be able to identify vulnerabilities manually and with nmap script scans, you aren’t allowed to use Nexpose, Nessus or any other vulnerability scanner during the exam.
- More importantly, don’t forget to use Exploit-db.com to search for Exploits.
- Use a good folder structure to organize your notes. For every machine I created a separate folder which contained relevant screenshots and scripts. I also stored my script (if re-usable) in a separate script folder. This can be handy for other machines, but also when doing the final exam.
- Last but not least… Try Harder!
Signing Up and Scheduling:
A quick note about signing up — they require that you use a non-free email address, so no @gmail, @yahoo, @live, etc…A work or school (.edu) email address will work. If you do not have a non-free email address that you can use then you will have to scan and email your ID.
Scheduling is another tough item to talk about for the course. You have the option to sign up for 30, 60, or 90 days of lab time, with the possibility of purchasing extensions later on (including a 15 day extension) if you need more time. It really comes down to a couple of things; how much time you have every day to devote to this course, and your knowledge/skill level going in. Most people I have talked to have needed to get extensions on their originally scheduled time.
If you have a full-time job, I would suggest at least scheduling 60 days. You can always order an extension later on if needed, and don’t ever be afraid to order one because most people also end up needing to.
The Course Material:
When you finally sign up and your start date comes around, you will receive an email containing download links for the lab manual, lab videos, your VPN connectivity pack, and the official PWK virtual machine. It is HIGHLY suggested that you use their Kali image (it is a 32-bit system), the course material was tested and run using this system. I have seen many people run into issues with the lab manual exercises because they did not use the provided Kali image.
You don’t have to go through the entire lab manual and all of the exercises, however I suggest you do. They go over a lot of the tools needed for the labs and you will most likely learn of new tools you had not heard of before. Plus, if you have no experience with Bash or Python, the lab material will give you some brief introductions to both.
The lab manual and lab videos are what make up the “course material” that I referenced previously. The manual is upwards of 350 pages long, with videos to accompany almost every section. When working through the manual I would read the pages first and then watch the accompanying video, but some people did it opposite of me or would watch the videos while reading the lab manual. Use whatever method works best for you.
The lab manual might seem huge, but it only covers part of what you will need for this course. This course should be thought of, and treated as, an almost entirely self-study style course. There are staff available to speak to for hints, however be expected to be told to “try harder”, and expect to do a lot of extra research.
Lab:
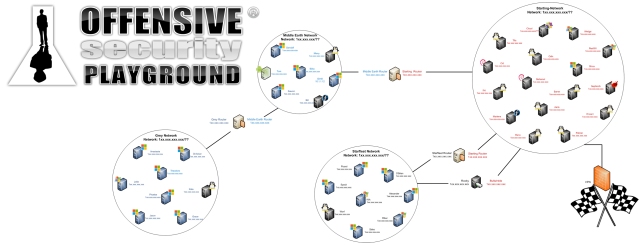
The PWK lab is really well designed. You are given access to about 60 disparate systems (varying OS’s, service packs/kernels, 3rd party software, etc), each with its own remote and local vulnerabilities waiting to be discovered. These systems span multiple networks, several of which are only accessible via exploitation and the various port redirection/tunneling techniques covered in the course. You should make an effort to access all networks, including Admin, and exploit as many systems as possible.
I recommend reverting (rebooting) each lab system before you try to exploit it. Remember that you’re in a lab environment with other students making changes to the same systems. There were a couple of instances when I forgot to revert a system and thought I had discovered an exploit only to find out it was put there by someone else. There will be times when you’re working on a system and someone else reverts it. While it is frustrating, it’s a fairly rare occurrence because there are so many systems across multiple lab networks and you’re limited in the number of available reverts per day (so use them sparingly!).
You will enjoy countless nights in the lab, befriending Bob, Alice, Bill, Sean and many others. If you are brave you can even take on Pain, Sufferance and Humble. The lab is vast and to be able to pass the exam, Offsec recommends at least getting all of the machines in the student network. One hint I also want to give is ‘keep it simple’. I’ve had it a few times that I was overthinking certain attack vectors, always start with the simple things.
The dual homed systems are great for practicing pivoting and attacking systems and networks though intermediary hosts. This often involves tunneling attacks through hosts you already control to circumvent firewall rules. Many of the vulnerabilities in the lab require you to download, fix and compile exploit code. Often in these cases the devil is in the very minor details and absolute focus and concentration is required to get an exploit to work the way you want it to.
After several months in the lab I managed to get into all of the networks, and get into all machines. This isn’t necessary to pass the exam, but you will be a lot more prepared if you do.
I learnt a few hard lessons here though. My initial approach was to start at one IP, and work my way through trying to pwn them. Once I reached a machine I could not crack, I decided to move on. This worked ok for a while, until I came to a point where I was not able to progress any further. I had to go back and loot the machines I had already pwnd, and that lead to learning more about the surrounding networks and their vulnerabilities.
Offensive Security have a mantra that many know. Try Harder. This is the classic response a student gets when asking for hints/help. It is probably the worst answer you can get when you have been bashing away at something for such a long time, but also the most rewarding when you finally get it.
pwning lab machines to prepare for the exam:
Many of the lab machines have vulnerabilities that have Metasploit modules. You can easily try the push button, get bacon technique on them. But, it is important to note that in the exam, you will be restricted to what you can use. In fact, there are very clear Metasploit restrictions. From not being allowed to use Metasploit at all, to only being allowed to use certain features of the meterpreter shell. With this in mind, I will always highly recommend you attempt to exploit as much as possible in the labs without the use of Metasploit.
Not being allowed to use Metasploit for me personally was not really such a big deal. Having practiced quite a lot in the labs to not use Metasploit, it was easy to find PoC exploits and modify them as required. I did make a lot of use of msfpayload to generate shellcode, but other than that, plain bind/netcat shells were in the order of the day.
Exam:
The exam is the hardest part. I recommend to structure all your scripts and pre-compile your most used local privilege escalation exploits. You don’t want to lose time on this during the exam. To pass the exam you need to have at least a certain amount of points. Each machine is worth a set amount of points and also has its own restrictions. As said before, you aren’t allowed to use Metasploit during the exam, except as a handler. If you like using meterpreter, know there are restrictions on which instructions you can use.
The exam was not easy in my experience, partially because you are very limited when it comes to using Metasploit. I wanted to get all the machines, but was not able to get root/administrator on all of them. I managed to get shells on all of them though.
Make sure you have a good lab report. If you don’t get enough points, they might accredit the few extra points needed if your lab report was exhaustive and written well.
My First attempt:
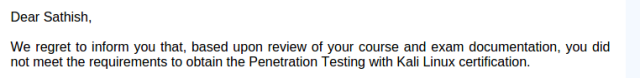
I was very confident, extremely confident, before taking my first shot at the exam. However, the first 18 hours flew very quickly and I’ve obtained only 50 points. I was stunned and could not cope with the fact that I would fail. After another 6 hours, from which only 2 hours sleeping, I had 65 points. A score that I did not expect whatsoever. At the last miniute i found a correct exploit for the 10 point machine, before work it out my VPN connection dropped and 24 hours get over. And I asked extra few minutes to the admin in IRC to work it out, but they told its an automatic thing so they cannot help me out in the suitation and they are strict with thier rules. So I totally Disappointed of my results I started writing the exam and lab report. I made a horrible report, probably because I knew that I will fail. The following days the result that I expected came by email: FAIL.
Second and final attempt:
I decided to start reading as much as I can about things that made me fail at my previous attempts. Blog posts, web-sites, tutorials, re-read the Offensive security materials, watched the whole videos again. Finally I understood what Abraham Lincoln meant when he said: Give me six hours to chop down a tree and I will spend the first four sharpening the axe. So I written a automatic script to enumerate all the boxes ones and compiled some exploits for Linux and Windows for Privileged esclation phase and collected a useful commands from my Lab notes and collected some shellcodes and revershell shell payloads. I decided to take the exam again after a week with full concentration and plenty of rest, and I pwned all 5 machine within 5 hours.
- If you have worked on Lab honestly , you would have gathered bunch of information, I would say compile those Links, Important and Handy Commands, and sort it carefully, which will save your time in exam
- Get complete rest before starting exam, Most importantly keep Coffee Packets Ready!
- If right before you start the exam, you have your playlist on random and the first song that plays is “The End” by The Doors, don’t panic, just laugh at the irony.
- Ping an admin on the IRC about 5-10 minutes before the exam starts. Start a private message chat and let them know you have an exam starting soon. Ask if you can PM them again if you have any questions once you receive and read the exam packet.
- Read Exam Instructions carefully word by word don’t miss any single word, else it will surely mess up.
- Define Max amount of time you will work on each machine, once time is up, move on to next box.
- Do not Update any tools before exam, it will mess up the stability, I updated one of the tool and had to spend 20 minutes on it, but was able to get rid of it.
- Take backups frequently, who knows VM may crash due to something…..
- Take as much screenshots as you can, step by step, Don’t forget to get important screenshot due to excitement, Its natural we get more excited when we get r00tw00t, and later on you realize about missing screenshots, name it appropriately, which will save your time while working on report.
- I would say, Attend all, struggle till last moment, don’t loose patience, at some point you may feel, you have enough points to pass exam, but trust me it can be an illusion, so always set goal to attend all!..
- Even if you are unable to get complete access, document your steps, it may help you.
- Enumeration is the key!…if you are unable to get direction loop it back to Enumeration step.
Reporting:
Penetration testing is as much about being able to find vulnerabilities in a network as it is about being able to represent this in report so that it is clear and understandable for people who might know less about security or who are not technical at all. In the end after pentesting, the only result for a client is the report. This part is not to be underestimated, I ended up writing around 400 pages of report. I first did the lab and then took another 14 days to write the report, it might be better to immediately write out everything.
The IRC Channel of OffSec:
As much as try harder was working for me it didn’t solve all my issues and I was quickly seeing my 90 days of lab time run out. Who can help me out? My friends and co-workers either don’t have the time or knowledge to help me.
I quickly found out that my feelings of hopelessness were shared amongst others within the PWK community. Emails started flying back and forth and information was being shared. Don’t misunderstand this. We were sharing information not giving answers away. At this point we were all trained in the “try harder” methodology and were not about to break it. You work extremely hard to get some boxes and you just aren’t about to give it away.
Along with IRC Offensive Security also provides students access to an online forum. These forums are full of great info. You know the normal stuff “Bob is laughing at you”, “try harder”, and then the helpful information. However being regulated by Offensive Security I don’t think that you will find any good hints or solutions to the labs in there. Again it’s about learning the lesson and not achieving the goal.
Finally, I would like to thank all of the admins and other users that I interacted with in the IRC for helping me out and share their experience with more fun. Among others:
rAWjAW
g0tmi1k_
ipchain
sickness
g11tch
Thiridium
r0t13
k3l00
sho_luv
sesses
karthik
morpheuss
Coming post i will share the tricks and things, that i learned and used during my labs and exam….