Google Finds 7 Security Flaws in Widely Used Dnsmasq Network Software
Security researchers have discovered not one or two, but a total of seven security vulnerabilities in the popular open source Dnsmasq network services software, three of which could allow remote code execution on a vulnerable system and hijack it.
Dnsmasq is a widely used lightweight network application tool designed to provide DNS (Domain Name System) forwarder, DHCP (Dynamic Host Configuration Protocol) server, router ads and network boot services for small networks.
Dnsmasq comes pre-installed on various devices and operating systems, including Linux distributions such as Ubuntu and Debian, home routers, smartphones and Internet of Things (IoT) devices. A shodan scan for “Dnsmasq” reveals around 1.1 million instances worldwide.
Recently, Google’s security team reviewed Dnsmasq and discovered seven security issues, including DNS-related remote code execution, information disclosure, and denial-of-service (DoS) issues that can be triggered via DNS or DHCP.
“We discovered seven distinct issues (listed below) over the course of our regular internal security assessments,” Google’s security team wrote in a blog post published on Monday.
“Once we determined the severity of these issues, we worked to investigate their impact and exploitability and then produced internal proofs of concept for each of them. We also worked with the maintainer of Dnsmasq, Simon Kelley, to produce appropriate patches and mitigate the issue.”
Since the vulnerabilities have now been patched by Dnsmasq developer and maintainer Simon Kelley, Google researchers have released details and proof-of-concept (PoC) exploit code for each of the vulnerabilities.
Out of seven vulnerabilities discovered by the team, three can be exploited to perform remote code execution, three can be used in denial of service attacks, and one information leakage flaw.
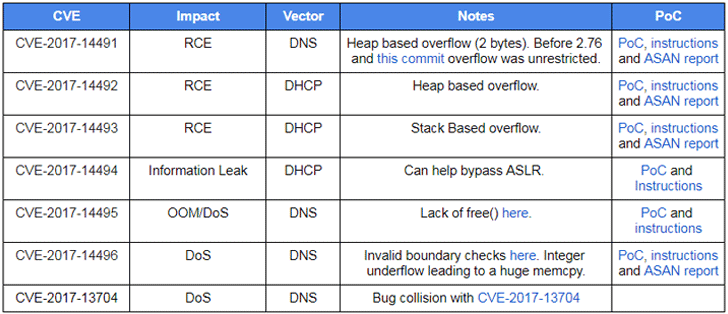
Here’s the List of All Vulnerabilities:
- CVE-2017-14491—A DNS-based remote code execution vulnerability in Dnsmasq versions before 2.76 is marked as the most severe that allows for unrestricted heap overflows, affecting both directly exposed and internal network setups.
- CVE-2017-14492—Another remote code execution vulnerability due to a DHCP-based heap overflow issue.
- CVE-2017-14493—Another noteworthy DHCP-based remote code execution bug caused by a stack buffer overflow. According to Google, this flaw is trivial to exploit if it’s used in conjunction with the flaw (CVE-2017-14494) mentioned below.
- CVE-2017-14494—An information leak in DHCP which can be combined with CVE-2017-14493 to allow attackers bypass ASLR security mechanism and execute arbitrary code on a target system.
- CVE-2017-14495—A flaw in Dnsmasq which can be exploited to launch a denial of service (DoS) attack by exhausting memory via DNS. The flaw impacts dnsmasq only if one of these options is used: –add-mac, –add-cpe-id or –add-subnet.
- CVE-2017-14496—Google’s Android operating system is specifically affected by this DoS issue which can be exploited by a local hacker or one who is tethered directly to the device. However, Google pointed out the service itself is sandboxed, so the risk to Android users is reduced.
- CVE-2017-14497—Another DoS issue wherein a large DNS query can crash the software.
Since all the issues have already been addressed with the release of Dnsmasq 2.78, Dnsmasq users are advised to update their installations as soon as possible.
To patch your devices, make sure to upgrade packages on your system. Google has updated its affected services and released the security fixes to Android partners on 5 September 2017 in October’s Android security updates.
Other affected Google services are also claimed to be updated. Kubernetes versions 1.5.8, 1.6.11, 1.7.7, and 1.8.0 have also been updated with a patched Dnsmasq.