Local privilege escalation with MS11-080
Not too long ago, I found myself in a need of escalating my privilege on a Windows box. JRE bugs look like the best bet here given the last year of endless Java bugs – but for some reasons I went for a year-old Windows bug instead: MS11-080.
Security bulletin from MS can be found here:
http://technet.microsoft.com/en-us/security/bulletin/ms11-080
Exploit code is avialable in Python right here:
It came in Python…… so a little more exercise was needed in order to make the exploit working right away on the machine with no Python installed. There are existing solutions out there to convert python scripts into executables on Windows. I used to have a good experience with py2exe long long time ago but nowadays it looks like PyInstaller is a more suitable option. Let’s go for PyInstaller 😀
PyInstaller is also capable of making executables for Linux, Mac OSX, Solaris and AIX! Very Nice 😀
So what will we need here are as follows:
(1) Python 2.7.x (Python3 not working with PyInstaller, it seems)
(2) pywin32 Using the version for Python2.7 ofc
(3) PyInstaller
(4) Yes, the sploit
Once we have everything setup, the process is straight forward. Get PyInstaller to create a nice exe for us 😀
c:>python pyinstaller.py –onefile ms11-080.py
If nothing goes nut, we’ll have an executable ready to exploit not-bothering-to-ptach server out there! 😀
We are most likely in a restricted environment, if we happen to need a privilege escalation like this. Therefore you may need to find a way to “run” the executable first to make this thing working, of course 😀
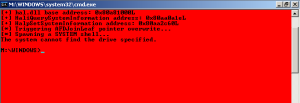
Running it in the GUI session and we would get a nice red SYSTEM-privilege cmd windows like this:
And, yeah, the original python code can be modified to just run a single command at your convenience – instead of spawning another shell. This might be useful if we need to run it in a remote shell or non-interactive web shell or such…